mirror of
https://github.com/amix/vimrc
synced 2025-09-19 11:14:59 +08:00
Updated plugins
This commit is contained in:
@ -1,9 +1,12 @@
|
||||
# nginx.vim
|
||||
|
||||
## Description
|
||||
|
||||
[Vim](http://www.vim.org/) plugin for [Nginx](http://www.nginx.org)
|
||||
|
||||
|
||||
## Features
|
||||
|
||||
The plugin is based on the recent vim-plugin distributed with `nginx-1.12.0` and additionally features the following syntax improvements:
|
||||
|
||||
- Highlight IPv4 and IPv6 addresses
|
||||
@ -24,6 +27,7 @@ Furthermore:
|
||||
|
||||
|
||||
## Screenshots
|
||||
|
||||
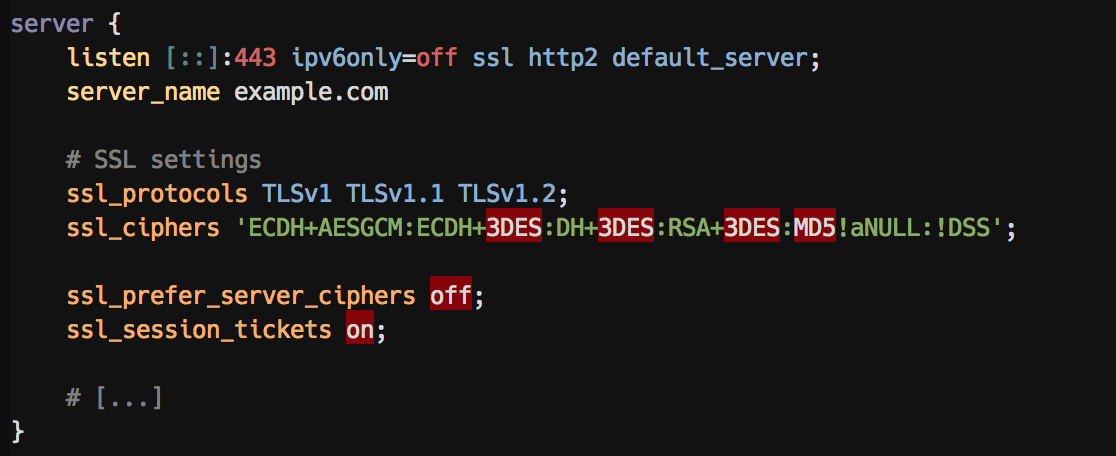
A `server` block with highlighting of insecure `ssl_protocol` options:
|
||||
|
||||
|
||||
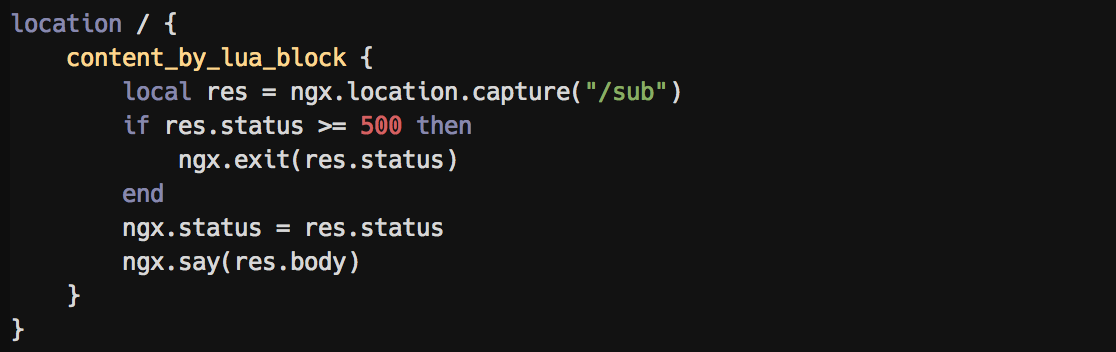
@ -37,46 +41,18 @@ Embedded LUA syntax highlighting:
|
||||
|
||||
|
||||
|
||||
## Snippets
|
||||
The plugin comes with useful snippets which can be accessed using e.g. [vim-snipmate](https://github.com/garbas/vim-snipmate).
|
||||
|
||||
Select a decent cipher for your requirements (all of them can provide [SSLLabs A+ ratings](https://www.ssllabs.com/ssltest/analyze.html))
|
||||
|
||||
- `ciphers-paranoid<tab>`: Even-more-secure ciphers (elliptic curves, no GCM), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android != 4.4
|
||||
- **`ciphers-modern<tab>`: High-security ciphers (elliptic curves), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android < 4.4 (recommended)**
|
||||
- `ciphers-compat<tab>`: Medium-security ciphers with good compatibility (No IE on WinXP) but TLSv1 and SHA required
|
||||
- `ciphers-old<tab>`: Low-security ciphers (using weak DES and SHA ciphers, TLSv1), but compatible with everything but IE6 and Java6
|
||||
- `ssl-options<tab>`: Bootstrap secure SSL options
|
||||
|
||||
Example:
|
||||
```nginx
|
||||
# High-security ciphers (elliptic curves), less compatibility
|
||||
# No IE < 10, OpenSSL-0.9.8, Safari < 7, Android < 4.4
|
||||
ssl_protocols TLSv1.1 TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
|
||||
```
|
||||
|
||||
Or add a robots.txt file with `robots.txt<tab>`:
|
||||
```nginx
|
||||
# Tell bots to not index this site
|
||||
location /robots.txt {
|
||||
default_type text/plain;
|
||||
return 200 'User-agent: *\nDisallow: /\n';
|
||||
}
|
||||
```
|
||||
|
||||
It also has auto-completion for location and server blocks with `location<tab>` resp. `server<tab>`, and [many more](https://github.com/chr4/nginx.vim/blob/master/snippets/nginx.snippets)!
|
||||
|
||||
- Add useful [snippets](https://github.com/chr4/nginx.vim/blob/master/snippets/nginx.snippets)
|
||||
|
||||
## References
|
||||
|
||||
- Based on the original `nginx-1.12.0/contrib/vim`
|
||||
- IPv4 and IPv6 address highlighting, based on expressions found in [this forum post](http://vim.1045645.n5.nabble.com/IPv6-support-for-quot-dns-quot-zonefile-syntax-highlighting-td1197292.html)
|
||||
- [Blog post](https://chr4.org/blog/2017/04/14/better-syntax-highlighting-and-snippets-for-nginx-in-vim/) introducing this plugin including some more examples
|
||||
|
||||
For help with secure cipher selection, visit [Mozillas SSL Configuration Generator](https://ssl-config.mozilla.org/)
|
||||
|
||||
## Installation
|
||||
|
||||
### Pathogen
|
||||
|
||||
```bash
|
||||
git clone https://github.com/chr4/nginx.vim ~/.vim/bundle/nginx.vim
|
||||
```
|
||||
|
||||
@ -1,166 +0,0 @@
|
||||
# vim: ft=nginx
|
||||
snippet l80
|
||||
listen [::]:80 ipv6only=off;
|
||||
$0
|
||||
|
||||
# Listen statements when using multiple http server blocks
|
||||
snippet l80-multi
|
||||
listen [::]:80 default_server;
|
||||
listen 80 default_server;
|
||||
$0
|
||||
|
||||
snippet l443
|
||||
listen [::]:443 ipv6only=off ssl http2 default_server;
|
||||
$0
|
||||
|
||||
# Listen statements when using multiple ssl server blocks
|
||||
snippet l443-multi
|
||||
listen [::]:443 ssl http2 default_server;
|
||||
listen 443 ssl http2 default_server;
|
||||
$0
|
||||
|
||||
# Cipher suites are taken and adapted from Mozilla's recommendations
|
||||
# https://wiki.mozilla.org/Security/Server_Side_TLS
|
||||
#
|
||||
# Paranoid mode
|
||||
snippet ciphers-paranoid
|
||||
# Paranoid ciphers, 256bit minimum, prefer ChaCha20/ Poly1305, bad compatibility
|
||||
# No Android 5+6 (4.4 works), Chrome < 51, Firefox < 49, IE < 11, Java 6-8, GoogleBot
|
||||
ssl_protocols TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384';
|
||||
$0
|
||||
|
||||
# Mozilla modern
|
||||
snippet ciphers-modern
|
||||
# High-security ciphers (elliptic curves), less compatibility
|
||||
# No IE < 10, OpenSSL-0.9.8, Safari < 7, Android < 4.4
|
||||
ssl_protocols TLSv1.1 TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
|
||||
$0
|
||||
|
||||
# Mozilla intermediate (Removed DES for more security)
|
||||
snippet ciphers-compat
|
||||
# Medium-security ciphers with good compatibility (Weak: SHA)
|
||||
# No IE on WinXP
|
||||
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:!DSS';
|
||||
$0
|
||||
|
||||
# Mozilla old (Removed DSS, HIGH, SEED for more security)
|
||||
snippet ciphers-low
|
||||
# Low-security ciphers (Weak: DES, SHA)
|
||||
# No IE6, Java6
|
||||
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDHE-ECDSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:DES-CBC3-SHA:!SEED:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!RSAPSK:!aDH:!aECDH:!KRB5-DES-CBC3-SHA:!SRP:!DSS';
|
||||
$0
|
||||
|
||||
snippet ssl-options
|
||||
# SSL certificate
|
||||
ssl_certificate /etc/nginx/certs/${4:www.example.com}.crt;
|
||||
ssl_certificate_key /etc/nginx/certs/${5:www.example.com}.key;
|
||||
# ssl_dhparam /etc/nginx/certs/dhparam.pem;
|
||||
|
||||
ssl_prefer_server_ciphers on;
|
||||
ssl_stapling off;
|
||||
ssl_stapling_verify off;
|
||||
ssl_session_cache 'shared:SSL:10m';
|
||||
ssl_session_tickets off;
|
||||
|
||||
# Enable HSTS (1 year) and some security options
|
||||
add_header Strict-Transport-Security 'max-age=31536000 includeSubDomains; preload;';
|
||||
$0
|
||||
|
||||
snippet security-headers
|
||||
add_header X-Frame-Options 'DENY';
|
||||
add_header X-Content-Type-Options 'nosniff';
|
||||
add_header X-Frame-Options 'SAMEORIGIN';
|
||||
add_header X-XSS-Protection '1; mode=block';
|
||||
add_header X-Robots-Tag 'none';
|
||||
add_header X-Download-Options 'noopen';
|
||||
add_header X-Permitted-Cross-Domain-Policies 'none';
|
||||
$0
|
||||
|
||||
snippet robots.txt
|
||||
# Tell bots to not index this site
|
||||
location /robots.txt {
|
||||
default_type text/plain;
|
||||
return 200 'User-agent: *\nDisallow: /\n';
|
||||
}
|
||||
$0
|
||||
|
||||
snippet basic-auth
|
||||
auth_basic 'Restricted';
|
||||
auth_basic_user_file ${1:/etc/nginx/htpasswd};
|
||||
$0
|
||||
|
||||
snippet proxy_pass
|
||||
proxy_pass_header Date;
|
||||
proxy_set_header X-Forwarded-Proto $scheme;
|
||||
proxy_set_header Host $host;
|
||||
proxy_set_header X-Real-IP $remote_addr;
|
||||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
|
||||
proxy_pass http://${1:backend};
|
||||
$0
|
||||
|
||||
snippet php-fpm
|
||||
location ~ \.php$ {
|
||||
include fastcgi_params;
|
||||
fastcgi_split_path_info ^(.+\.php)(/.+)$;
|
||||
fastcgi_index index.php;
|
||||
fastcgi_intercept_errors on;
|
||||
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
|
||||
fastcgi_pass ${1:127.0.0.1:9000};
|
||||
}
|
||||
$0
|
||||
|
||||
snippet php-uwsgi
|
||||
location ~ \.php$ {
|
||||
include uwsgi_params;
|
||||
uwsgi_max_temp_file_size 4096m;
|
||||
uwsgi_modifier1 14;
|
||||
uwsgi_read_timeout 900;
|
||||
uwsgi_send_timeout 900;
|
||||
uwsgi_pass ${1:unix:///run/uwsgi/php.sock};
|
||||
}
|
||||
$0
|
||||
|
||||
snippet redirect-ssl
|
||||
location / {
|
||||
return 301 https://$http_host$request_uri;
|
||||
}
|
||||
$0
|
||||
|
||||
snippet redirect-other
|
||||
# Redirect other requested hosts
|
||||
if ($host != '${1:DOMAIN}') {
|
||||
return 301 https://${2:DOMAIN}$request_uri;
|
||||
}
|
||||
$0
|
||||
|
||||
snippet letsencrypt
|
||||
listen [::]:80 ipv6only=off;
|
||||
|
||||
# Serve well-known path for letsencrypt
|
||||
location /.well-known/acme-challenge {
|
||||
root /etc/nginx/certs/acme;
|
||||
default_type text/plain;
|
||||
}
|
||||
|
||||
location / {
|
||||
return 301 https://$http_host$request_uri;
|
||||
}
|
||||
$0
|
||||
|
||||
snippet cut-trailing-slash
|
||||
rewrite ^/(.*)/$ $scheme://$http_host:$server_port/$1 permanent;
|
||||
$0
|
||||
|
||||
snippet location
|
||||
location ${1:/} {
|
||||
${0:${VISUAL}}
|
||||
}
|
||||
|
||||
snippet server
|
||||
server {
|
||||
${0:${VISUAL}}
|
||||
}
|
||||
Reference in New Issue
Block a user