mirror of
https://github.com/amix/vimrc
synced 2025-09-19 11:14:59 +08:00
Updated plugins
This commit is contained in:
@ -1,9 +1,12 @@
|
||||
# nginx.vim
|
||||
|
||||
## Description
|
||||
|
||||
[Vim](http://www.vim.org/) plugin for [Nginx](http://www.nginx.org)
|
||||
|
||||
|
||||
## Features
|
||||
|
||||
The plugin is based on the recent vim-plugin distributed with `nginx-1.12.0` and additionally features the following syntax improvements:
|
||||
|
||||
- Highlight IPv4 and IPv6 addresses
|
||||
@ -24,6 +27,7 @@ Furthermore:
|
||||
|
||||
|
||||
## Screenshots
|
||||
|
||||
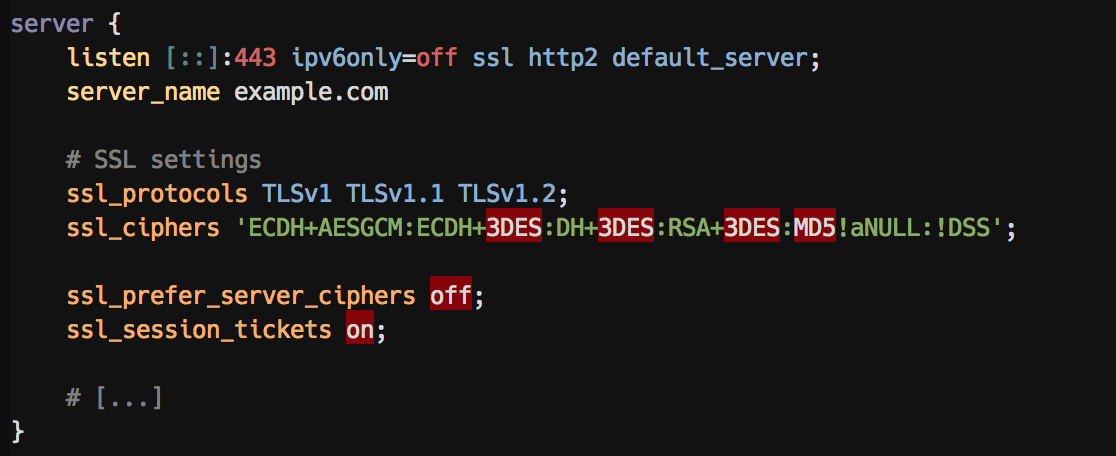
A `server` block with highlighting of insecure `ssl_protocol` options:
|
||||
|
||||
|
||||
@ -37,46 +41,18 @@ Embedded LUA syntax highlighting:
|
||||
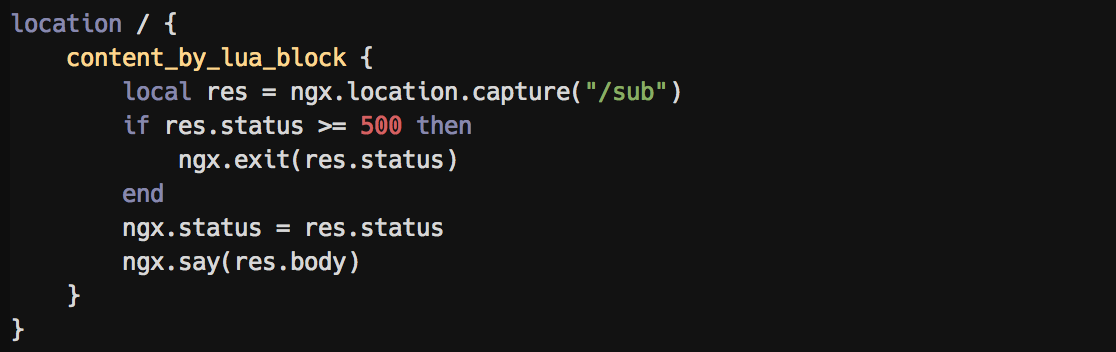
|
||||
|
||||
|
||||
## Snippets
|
||||
The plugin comes with useful snippets which can be accessed using e.g. [vim-snipmate](https://github.com/garbas/vim-snipmate).
|
||||
|
||||
Select a decent cipher for your requirements (all of them can provide [SSLLabs A+ ratings](https://www.ssllabs.com/ssltest/analyze.html))
|
||||
|
||||
- `ciphers-paranoid<tab>`: Even-more-secure ciphers (elliptic curves, no GCM), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android != 4.4
|
||||
- **`ciphers-modern<tab>`: High-security ciphers (elliptic curves), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android < 4.4 (recommended)**
|
||||
- `ciphers-compat<tab>`: Medium-security ciphers with good compatibility (No IE on WinXP) but TLSv1 and SHA required
|
||||
- `ciphers-old<tab>`: Low-security ciphers (using weak DES and SHA ciphers, TLSv1), but compatible with everything but IE6 and Java6
|
||||
- `ssl-options<tab>`: Bootstrap secure SSL options
|
||||
|
||||
Example:
|
||||
```nginx
|
||||
# High-security ciphers (elliptic curves), less compatibility
|
||||
# No IE < 10, OpenSSL-0.9.8, Safari < 7, Android < 4.4
|
||||
ssl_protocols TLSv1.1 TLSv1.2;
|
||||
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
|
||||
```
|
||||
|
||||
Or add a robots.txt file with `robots.txt<tab>`:
|
||||
```nginx
|
||||
# Tell bots to not index this site
|
||||
location /robots.txt {
|
||||
default_type text/plain;
|
||||
return 200 'User-agent: *\nDisallow: /\n';
|
||||
}
|
||||
```
|
||||
|
||||
It also has auto-completion for location and server blocks with `location<tab>` resp. `server<tab>`, and [many more](https://github.com/chr4/nginx.vim/blob/master/snippets/nginx.snippets)!
|
||||
|
||||
- Add useful [snippets](https://github.com/chr4/nginx.vim/blob/master/snippets/nginx.snippets)
|
||||
|
||||
## References
|
||||
|
||||
- Based on the original `nginx-1.12.0/contrib/vim`
|
||||
- IPv4 and IPv6 address highlighting, based on expressions found in [this forum post](http://vim.1045645.n5.nabble.com/IPv6-support-for-quot-dns-quot-zonefile-syntax-highlighting-td1197292.html)
|
||||
- [Blog post](https://chr4.org/blog/2017/04/14/better-syntax-highlighting-and-snippets-for-nginx-in-vim/) introducing this plugin including some more examples
|
||||
|
||||
For help with secure cipher selection, visit [Mozillas SSL Configuration Generator](https://ssl-config.mozilla.org/)
|
||||
|
||||
## Installation
|
||||
|
||||
### Pathogen
|
||||
|
||||
```bash
|
||||
git clone https://github.com/chr4/nginx.vim ~/.vim/bundle/nginx.vim
|
||||
```
|
||||
|
||||
Reference in New Issue
Block a user