nginx.vim
Description
Features
The plugin is based on the recent vim-plugin distributed with nginx-1.12.0 and additionally features the following syntax improvements:
- Highlight IPv4 and IPv6 addresses
- Mark insecure
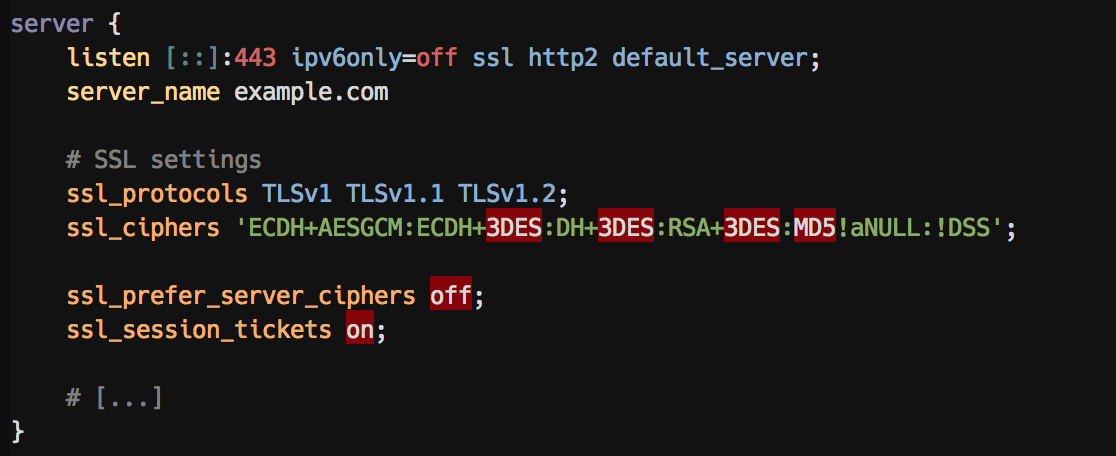
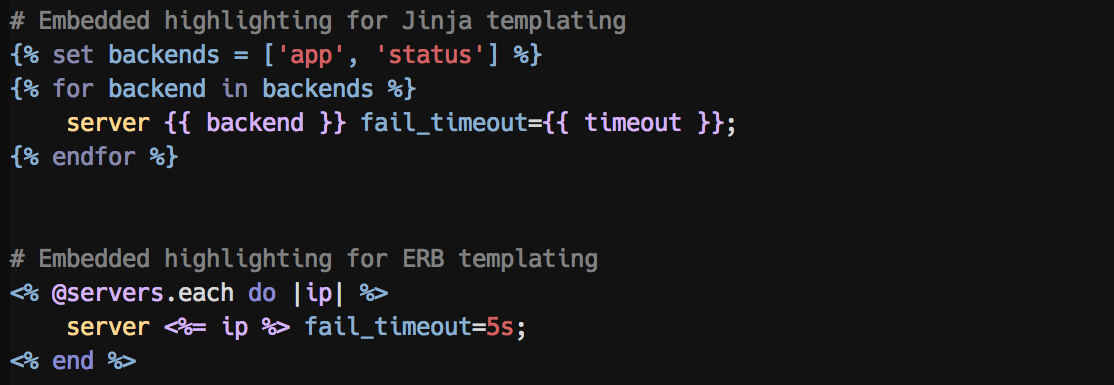
ssl_protocolsas errors - Inline template syntax highlight for ERB and Jinja
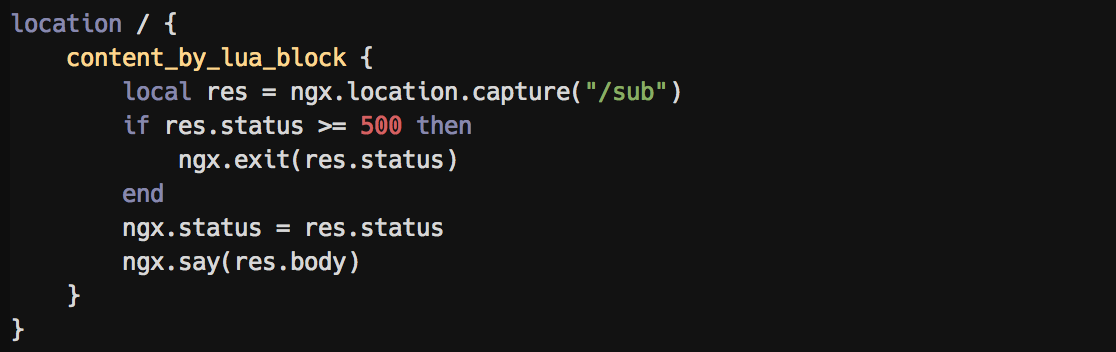
- Inline syntax highlight for LUA
- Improve integer matching
- Syntax highlighting for
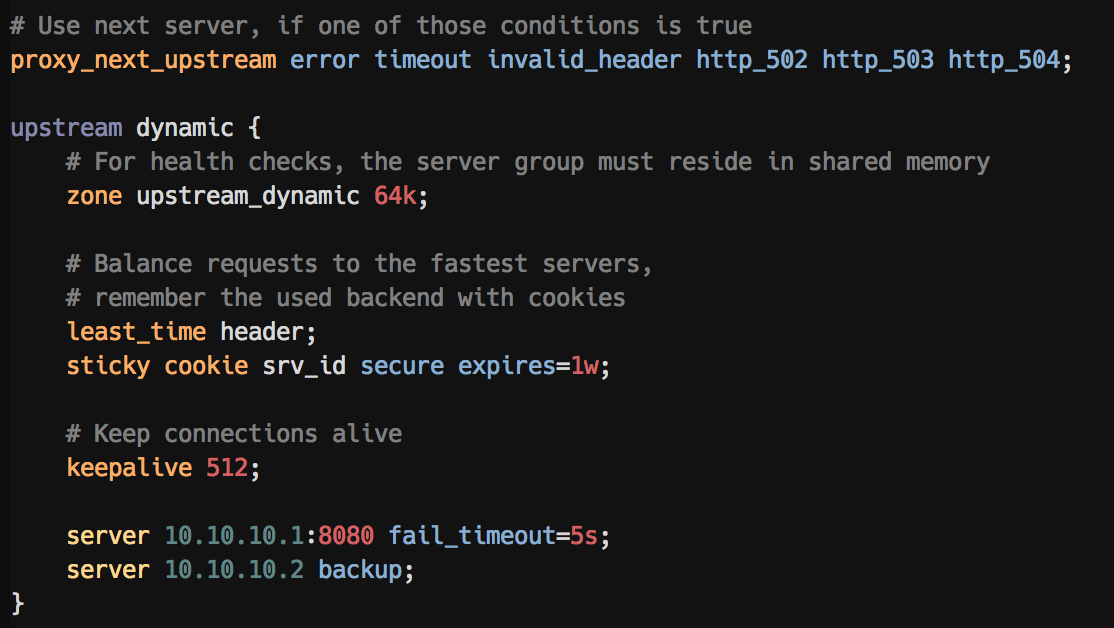
proxy_next_upstreamoptions - Syntax highlighting for
stickyoptions - Syntax highlighting for
upstreamserveroptions - More to come!
Furthermore:
- Remove annoying delimiters, resulting in strange word-boundaries
Note: Also check out sslsecure.vim: it supports highlighting insecure SSL/TLS cipher suites and protocols in all your files!
Screenshots
A server block with highlighting of insecure ssl_protocol options:
An upstream block with highlighted options:
Embedded highlighting for ERB and Jinja templates:
Embedded LUA syntax highlighting:
Snippets
The plugin comes with useful snippets which can be accessed using e.g. vim-snipmate.
Select a decent cipher for your requirements (all of them can provide SSLLabs A+ ratings)
ciphers-paranoid<tab>: Even-more-secure ciphers (elliptic curves, no GCM), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android != 4.4ciphers-modern<tab>: High-security ciphers (elliptic curves), not compatible with IE < 11, OpenSSL-0.9.8, Safari < 7, Android < 4.4 (recommended)ciphers-compat<tab>: Medium-security ciphers with good compatibility (No IE on WinXP) but TLSv1 and SHA requiredciphers-old<tab>: Low-security ciphers (using weak DES and SHA ciphers, TLSv1), but compatible with everything but IE6 and Java6ssl-options<tab>: Bootstrap secure SSL options
Example:
# High-security ciphers (elliptic curves), less compatibility
# No IE < 10, OpenSSL-0.9.8, Safari < 7, Android < 4.4
ssl_protocols TLSv1.1 TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
Or add a robots.txt file with robots.txt<tab>:
# Tell bots to not index this site
location /robots.txt {
default_type text/plain;
return 200 'User-agent: *\nDisallow: /\n';
}
It also has auto-completion for location and server blocks with location<tab> resp. server<tab>, and many more!
- Add useful snippets
References
- Based on the original
nginx-1.12.0/contrib/vim - IPv4 and IPv6 address highlighting, based on expressions found in this forum post
- Blog post introducing this plugin including some more examples
Installation
Pathogen
git clone https://github.com/chr4/nginx.vim ~/.vim/bundle/nginx.vim
Other (Plug, Dein.vim, Vundle)
" Plug
Plug 'chr4/nginx.vim'
" Dein.vim
call dein#add('chr4/nginx.vim')
" Vundle
Plugin 'chr4/nginx.vim'
Optionally, if you like Jinja template syntax highlighting, install lepture/vim-jinja, too.